Discover the prowess of ETCETERA® ECM (Enterprise Content Management), your go-to module for browser-based document and file management catering to a plethora of purposes. As a mature fourth-generation product, ECM stands out with its high customization potential, eliminating the need for a Windows client, and facilitating in-browser scanning at fully rated speeds.
Unlock a wealth of file accessibility with ECM, capable of storing and accessing 100 different file types through a Scalable Vector Graphics (SVG) viewer. Enjoy the modern touch of HTML5 support and mobile device accessibility, ensuring your documents are always within reach, anytime, anywhere.
Step into a realm where organization meets technology. ECM serves as a robust platform to organize, acquire, catalog, and access documents and files of varying types. With customer-managed applications configured in ECM, enjoy the liberty to organize your documents in classes defined by you, ensuring a tailored fit for your organizational needs.
Ease into content acquisition and accessibility with ECM. Experience seamless content interaction from diverse sources right within the application. Extend the functionality with content-enabled EPM and smooth integration with other applications such as your corporate ERP, all streamlined into three simple stages for an uncomplicated, efficient document management journey.
The User Experience
Making Work as Simple as 1 – 2 – 3
1
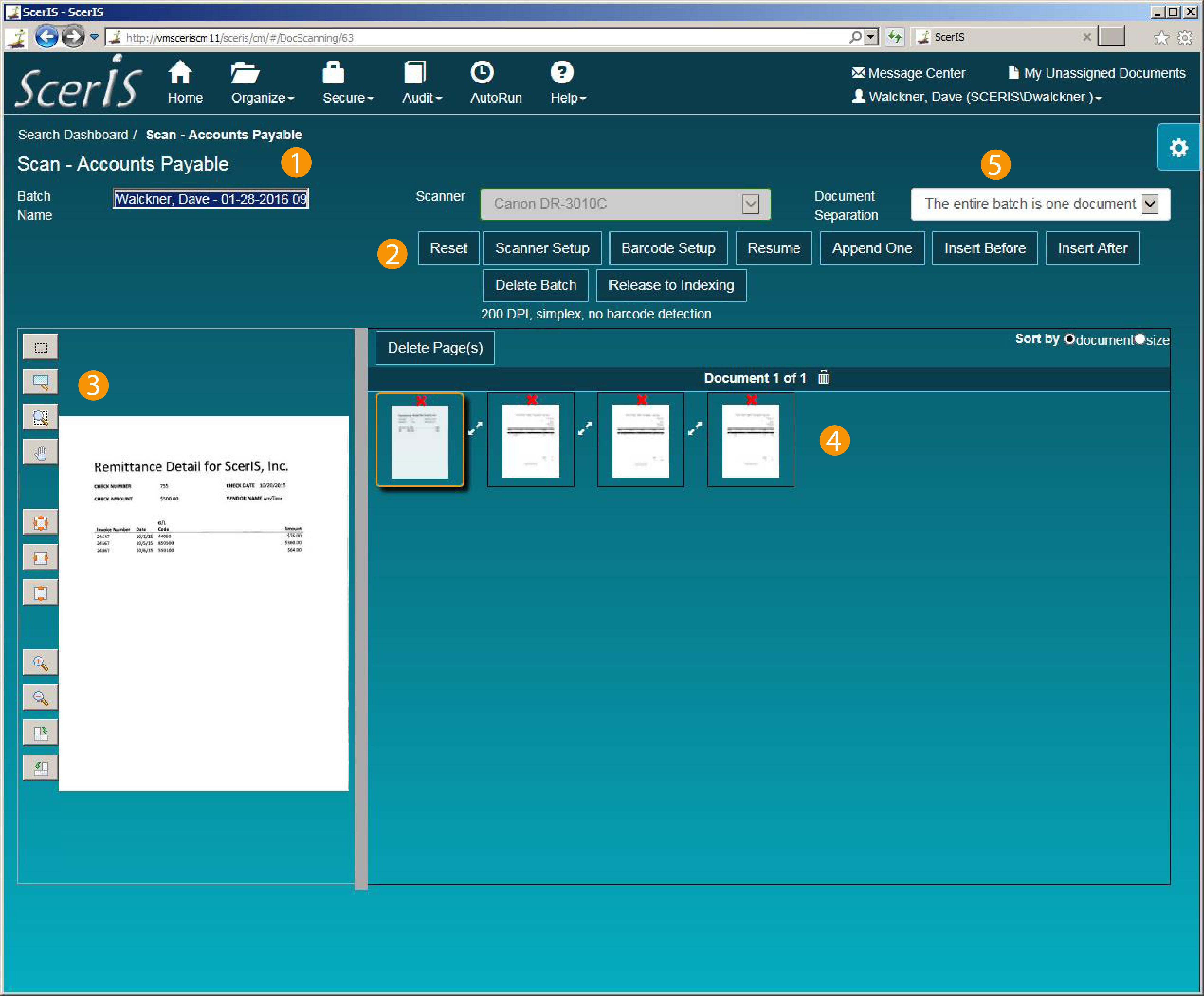
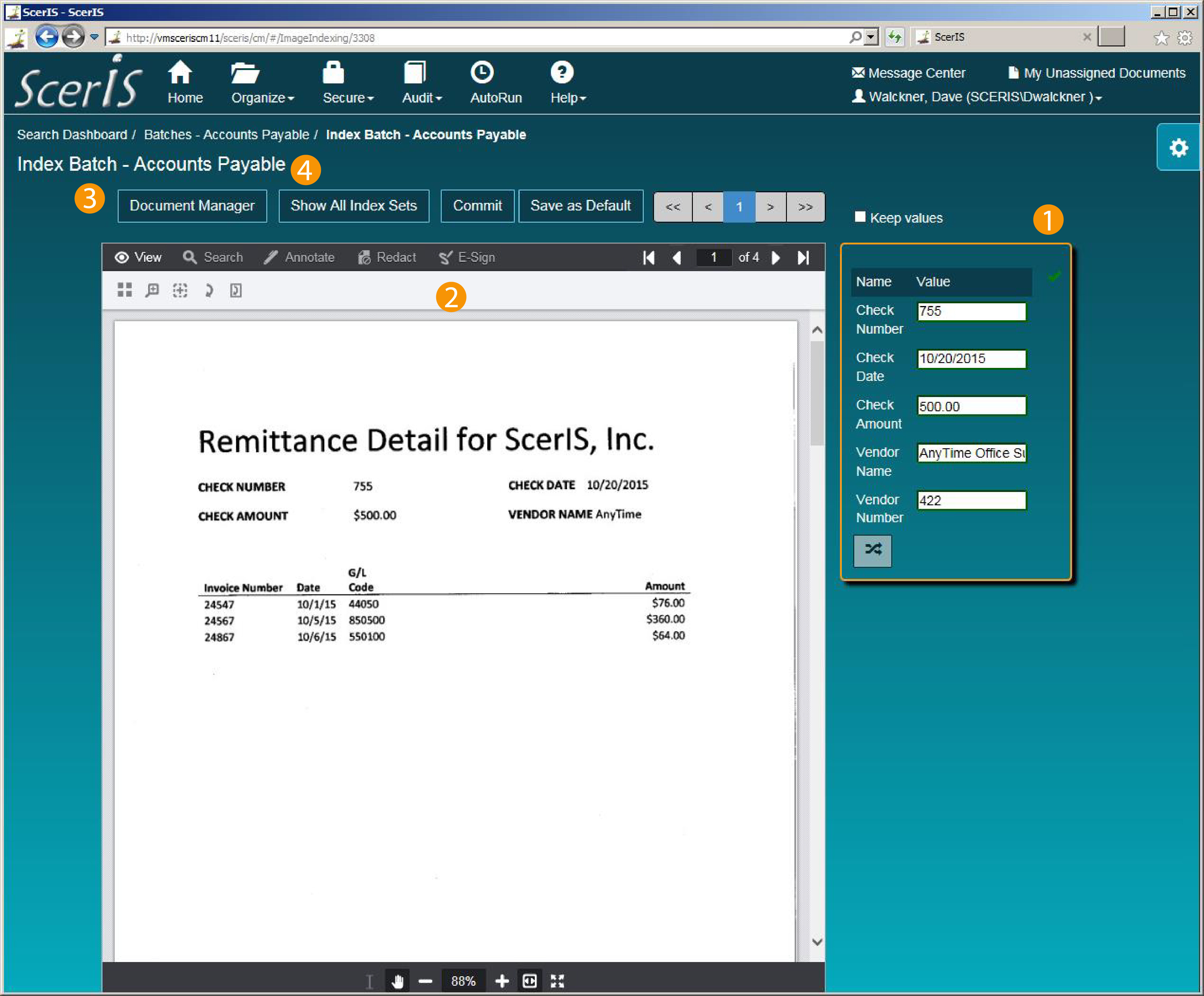
Capture
2
Index

3
Access
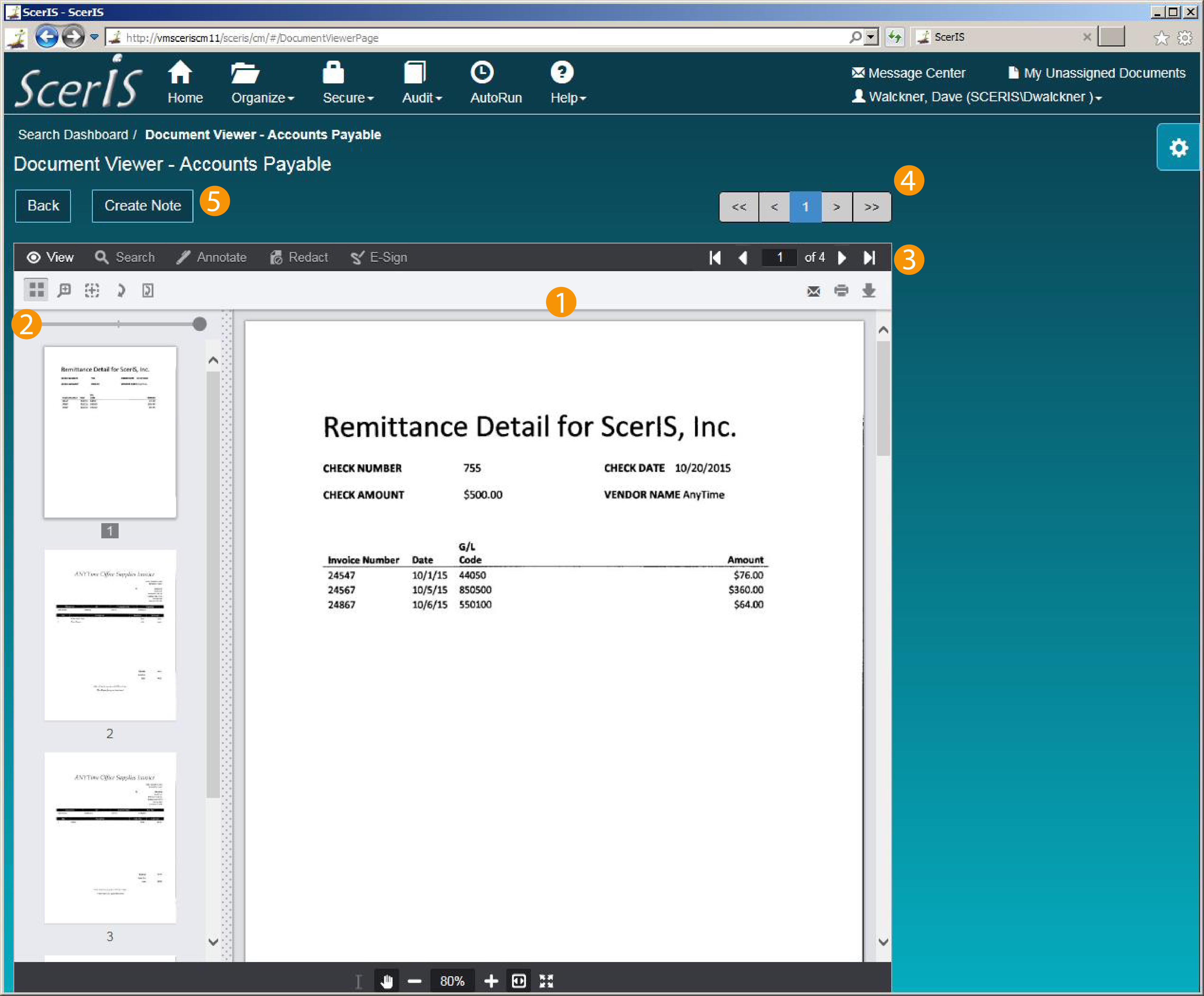
Release of Information
Some environments require documenting the Release of Information (ROI). ROI is configured by Folder and can include preconfigured reasons and require the user to complete information prior to printing, faxing or downloading documents.
Restricting Access
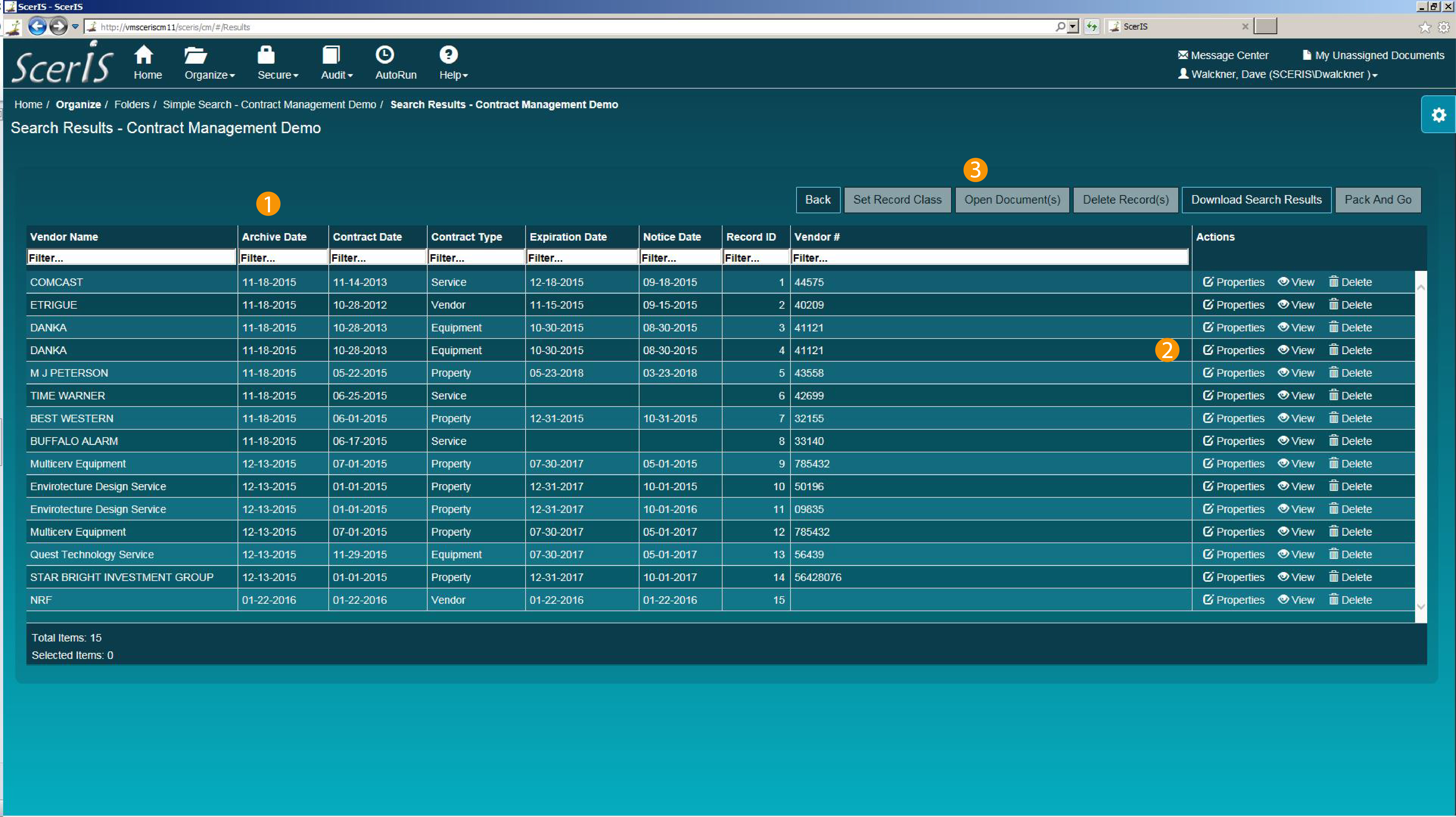
Security can be applied to Folders, Documents, Notes and Folder Collections. Additionally, security applied to documents can be automated based on an index value. Any Folder, Document, Note or Folder Collection that is not accessible by a user is not displayed for the user and they are unaware of its existence.
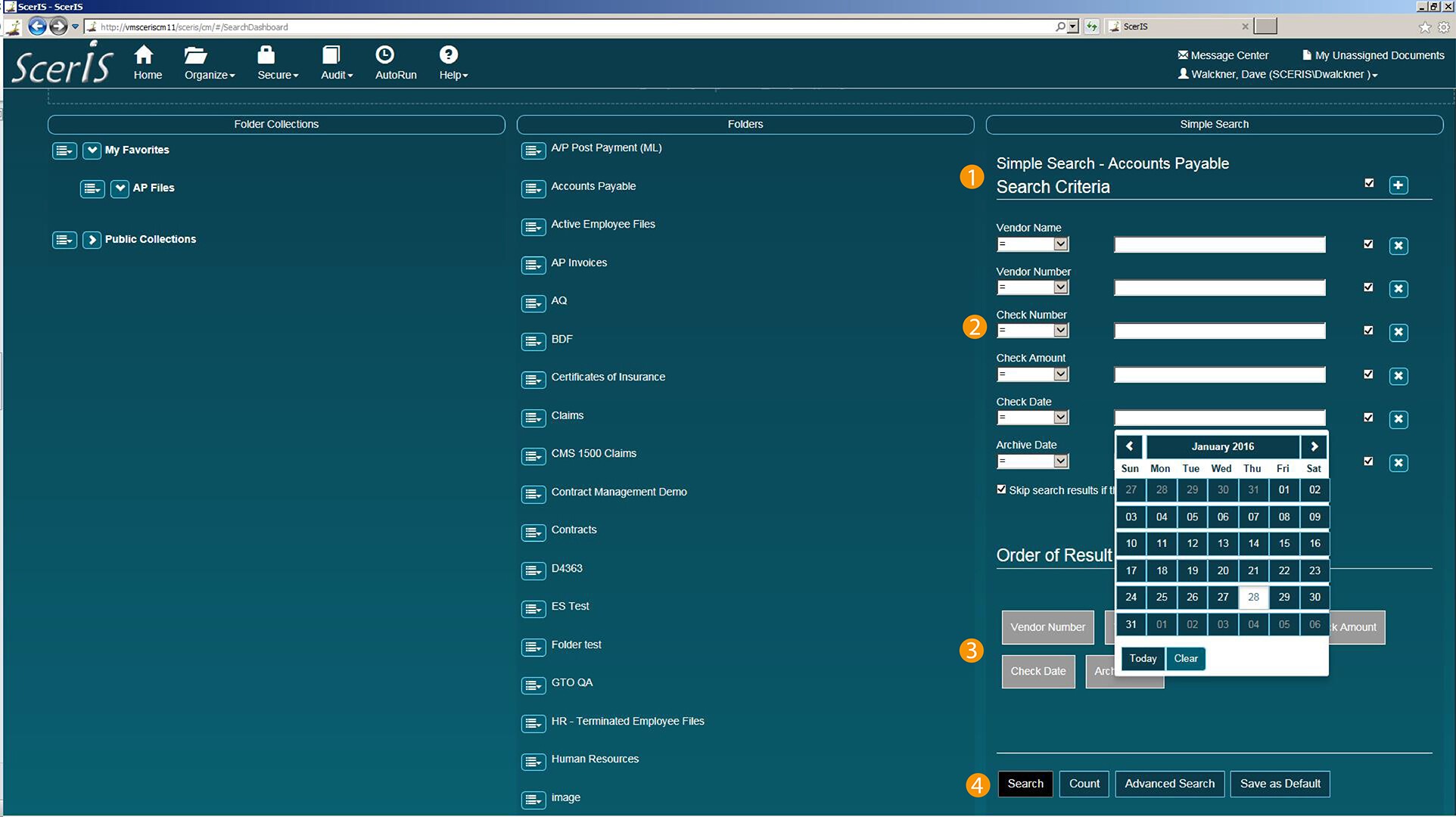
Accessing Audit Reports
Numerous Audit Reports are preconfigured and available. Additionally, using Microsoft Analysis Services and Reporting Services (or Crystal Reports or another Report Writer), custom reports are easily deployed. Preconfigured reports include:
- Queries in a Folder
- Document Views in a Folder
- Document Commits in a Folder
- Search Results Viewed
- Records Deleted
- Prints, Exports and Emailed Documents of a Folder
- Changed Indexes Report
- Changed Record Classes Report
- Documents Prepped
- Documents Scanned
- Documents Indexed
Setting Up User Permissions
User security and permissions are managed in Authorization Services (AUTH). The AUTH architecture provides a very granular authorization security schema where security definitions are comprised of Objects, Access Conditions, Resources, Actions, Permissions, Groups, and Users. AUTH is integrated to Active Directories for Single Sign-On and also provides for ScerIS Named Users. ScerIS software products sense Windows authentication in permitting access to applications and in determining other user specific privileges.